
E-mail isn’t secure. It passes through many strange networks. It can be examined. It can be spoofed. It can be tampered with. It can be kept when you want it to be discarded. It can carry so many nasty surprises. When using it, you need to be on your guard.
So let us help you out, Moses style:
-
Thou shalt not click the links in messages.
If an e-mail has a hyperlink to your bank — or some other website you would provide confidential information to — do not click or follow the link! It is very easy to “spoof” a link (i.e. making a link display as https://www.mybank.com, yet having it forward to http://www.badguy.net). It is better to copy the link to the clipboard and paste it into your browser. That way, you can inspect the real link URL before you submit it.
-
Thou shalt not suffer a client to show pictures.
Pictures embedded within e-mail messages can be used to track reading habits. In some extreme circumstances, e-mail images have even been used to successfully infect the reader’s computer. If your mail client has an option to not show pictures, take advantage of it. If your mail client does not have this option, use one that does.
-
Thou shalt not forward chain messages.
Many chain e-mails can contain bugs (transparent images and pieces of JavaScript hidden in an e-mail to track viewers, scrape e-mail addresses for spamming, and possibly deliver a virus payload). If it is an important message, just re-type a quick summary of it in a new message.
-
Honour thy confidential information and do not e-mail it.
All e-mail transferred over the internet can be read by at least two servers, and possibly several networks along the way. Never send confidential information via e-mail. If someone has sent confidential information to you via e-mail, change what you can (passwords and such), then ask the sender to refrain from doing so in the future.
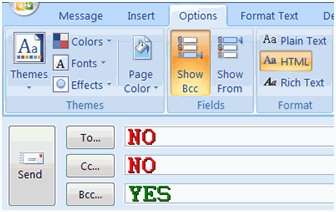
Remember the Bcc field, and keep it holy.
-
Thou shalt not use the Cc or To fields in vain.
If you To or Cc a message to multiple recipients, each recipient will see the e-mail address (and possibly the name) of everyone else that you sent the message to. When we Cc and To multiple recipients, we are needlessly spreading e-mail addresses into other peoples’ inboxes. Many viruses go straight for the inbox to begin relaying spam. Bcc recipients only see their own e-mail address in the To field. When you use Bcc instead, you are helping to preserve the privacy and security of your friends, family, and co-workers.
-
Thou shalt not use insecure webmail.
If you use a web-based e-mail service like Yahoo!, Hotmail, or Gmail in your browser, make sure that you are using HTTPS in your browser instead of HTTP to get to the website. You will know that you are using HTTPS when you see https:// at the beginning of the address, the security lock appears, and the lock is fully closed.
-
Thou shalt not use insecure mail protocols.
If you use an e-mail client (a program that runs on your device, like iPhone Mail, Android Mail, Microsoft Outlook or Mozilla Thunderbird), you are probably directly using SMTP to send e-mail and IMAP or POP3 to receive e-mail. When using these protocols, make sure that you are using the secure versions of them.
Typically, SMTP/S uses SSL over port 465, POP3/S uses SSL over port 995, and IMAP/S uses SSL over port 993. Unfortunately, these settings vary from provider to provider, so if you are interested in setting up secure mail, you may need to ask your e-mail provider for the proper settings.
-
Thou shalt not open unto thee any active attachments.
For safety, limit yourself to images (JPG, GIF, PNG) and PDFs. Even those are not perfectly safe. Everything else has a lot of potential for harm, especially on Windows:
Extension Type Danger =============================================================== EXE, COM, PIF, SCR Windows Executable HIGH APPLICATION, MSC Windows Executable HIGH GADGET, HTA, CPL, BAT Windows Executable HIGH MSI, MSP Windows Installer HIGH VB, VBS, VBE MS Visual Basic HIGH WS, WSF, WSC, WSH Windows Script HIGH PS* Windows PowerShell HIGH REG Windows Registry HIGH SCF Windows Explorer HIGH LNK Windows Shortcut HIGH INF Windows AutoRun HIGH SH, BASH, CSH, ZSH Unix Script HIGH JAR Java Application HIGH JS, JSE JavaScript HIGH ZIP, CAB, RAR Compressed Archive MEDIUM DOCM, DOTM, XLSM, XLTM Microsoft Office Macro MEDIUM XLAM, PPTM, POTM, PPAM Microsoft Office Macro MEDIUM PPSM, SLDM Microsoft Office Macro MEDIUM DOC, XLS, PPT Legacy Microsoft Office MEDIUM DOCX, XLSX, PPTX Microsoft Office 2007+ LOW
-
Thou shalt not leak thy neighbour’s e-mail addresses, nor his telephone numbers, nor any other thing that is thy neighbour’s to apps and websites.
Many apps and websites have a “find friends in contacts” feature that requests permission to read your address book. If you care about your contacts and their privacy, give that request a hard NO. If you don’t, in the best case your contacts will end up with more spam. In the worst case, they could have their identities leaked to those who do not wish them well.
Facebook and others link e-mail addresses, telephone numbers, and almost any other piece of data they get to profiles. You can search for profiles with some of that data. Great for reconnecting with old friends! Also great for cyberstalking people.