When Information Technology (IT) is working, it is a force-multiplier that lets you do more with less.
When IT is not working, loss and liability typically ensue: Internet and power outages become lost sales. Data breaches can lead to loss of customers, legal liability, and a damaged reputation. Lost or corrupted data—like customer lists or market data—can result in missed sales, marketing, and tax opportunities.
Having your systems fully-operational while the competitions’ are in disarray is a huge opportunity. Here are a few basic pieces of practice and equipment (that almost every business can afford) to keep your systems working and your opportunities open:
The Basics
Uninterruptible Power Supply (UPS)

An uninterruptible power supply is a surge protector with a battery. It protects your equipment from voltage spikes, brownouts, and power outages.
Smaller ones hold just enough power to save your work and cleanly shut down. Larger ones can power equipment for hours or even days.
If you only use a laptop, an ordinary surge protector will do—laptops already have batteries.
A decent one can be picked up at almost any office store for under $50. If you don’t have one, get one.
Redundant Array of Independent Disks (RAID)

Generally speaking, the most valuable part of a business system isn’t the hardware—it’s the data! The data is stored on a component called the hard drive. Unfortunately, hard drives are one of the more failure-prone components of a computer.
RAID is a technology for duplicating data and parity information across multiple disks so that failure of a single disk (or even multiple disks in some cases) does not result in data loss.
NOTE: RAID is not a substitute for making backups. RAID duplicates data in real-time and offers some protections against downtime and data loss from hardware failure. It does not protect against data loss and corruption from software and user errors. If I accidentally wipe a file on a RAID array, it is wiped from all of the drives in the array. I would need to pull a copy from backup to restore it.
Strict Permissions
In many systems, default permissions are too permissive. If you have shared resources—like a file share or an online service—take the time to set permissions for each user so that they have access to only what they need.
Permissions that are too loose can lead to adverse consequences, such as: malware infection, data loss, data corruption, blackmail, breach of confidentiality, and liability.
For instance, we have found that running Windows under a limited user account instead of the default full administrator account can reduce malware infection rates by over 90%.
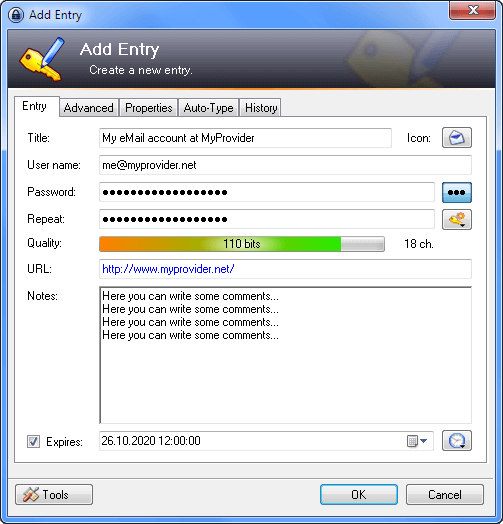
Password Management Software (Encrypted)
Using the same password for everything is trouble waiting to happen. Writing different passwords on a sheet of paper in your desk is the same story.
A password management program stores your user names and passwords in a single database that is encrypted with a single password. Password management software makes it easy to find accounts, manage them, and use different passwords for different services. Most packages also have a “print” feature for making a hard copy you can put in your safe.
We recommend the free open-source KeePass Password Safe. Command-line groupies may prefer pass: the standard Unix password manager.
System Restore (Windows)
Every version of Microsoft Windows since Windows XP has a feature called System Restore. System Restore lets the user dial back the clock to an earlier working state.
If you suspect your Windows machine has been infected, or has taken some other turn for the worse, try shutting it down and attempt a System Restore.
How to perform a System Restore:
- Shut down.
- Restart your computer while repeatedly pressing the F8 key.
- At the “Advanced Boot Options” prompt, select Safe Mode with Command Prompt.
- Press Enter
- Type: rstrui.exe
- Press Enter
- Follow the on-screen instructions to choose an available restore point to restore from.
Spare Hardware (Pre-configured)
If it’s in the budget, having a pre-configured spare that can be quickly swapped-in can be a worthwhile investment.
Some enterprise support contracts will “guarantee” four-hour support windows. I have had vendors (names withheld to protect the guilty) tell me that by answering my call within four hours they have fulfilled their obligation, and that the actual replacement part will not arrive until next week!
In many cases, having a spare on-hand is less stressful and more economical than keeping up a “four-hour support” contract.
Portable VOIP
Most voice over IP (VOIP) services have a routing feature where you can quickly re-route your office number to your computer, a cell phone, or another land line when the office is down. This can be a life-saver during a natural disaster or a prolonged internet outage.
Here are a few popular VOIP services in 2017:
- 8×8
- Fonality
- Nextiva
- Ooma
- RingCentral
- Skype
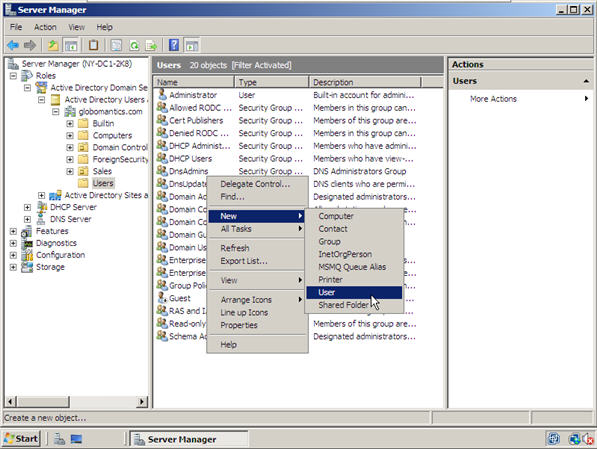
Single Sign-On
A single sign-on (SSO) service (like Microsoft’s Active Directory) allows management of multiple user accounts from one place.
Without SSO, it is possible for an employee to change a password to a critical system, then disappear—leaving you locked out of your own stuff!
With SSO, you have a master account that can change access levels and passwords for subordinate users. If an employee forgets his password, you can change it. If an employee quits unexpectedly, you can revoke his access to all business systems in one place.
Emergency Mail Hosting

E-mail has become a critical business system. When it comes to such things, better not have all of your eggs in the same basket.
No matter how great GMail and hosted Exchange are, anything can fail. Basic mail hosting is so inexpensive these days that keeping a second pre-configured mail host in the wings is a guaranteed win. That way, if the primary service fails, just change your MX record to the emergency mail host, and the mail will keep flowing.
We offer basic POP/IMAP/SMTP e-mail hosting for $25 per year per inbox.
Friendly Neighborhood IT Contractor

The unexpected happens: family emergencies, prolonged illnesses, irreconcilable differences… the list goes on and on.
It’s good to keep in touch with someone on the outside. Someone you can depend on to keep things running until more permanent arrangements can be made. hint hint
Backups!
This is more along the lines of disaster recovery, but it can’t be stated enough: Back that stuff up!
A few backup tips:
- Do it regularly, preferably on a schedule.
- Keep copies off-site.
- Automate it as much as possible with: scripts, cloud backup services, rsync, tape jukeboxes, and the like.
- Stagger your backup media! For example: have one media rotation for daily backups and a separate rotation for monthly ones. That way, if you don’t notice something is missing until after it has been missed in a daily rotation, chances are it will still be in the monthly rotation.
- Ensure that your backups are fully recoverable with occasional test restores to a non-production machine.
And for extra credit…
Shadow Copy (Windows)
For some time now, enterprise and professional versions of Microsoft Windows have shipped with a feature called Shadow Copy. Shadow copy makes scheduled snapshots of files and folders that can be reverted to in the event of a deletion or a mistake.
To enable Shadow Copy for a drive:
- Right-click on the drive in Explorer and choose the Properties command.
- In the disk properties dialog, go to the Shadow Copies tab. In this tab you can configure the amount of space reserved for Shadow Copies as well as the snapshotting schedule.
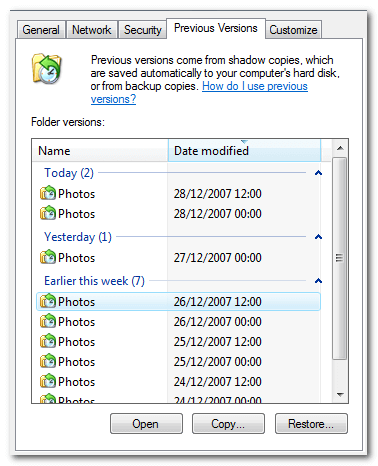
To restore deleted files/folders using Shadow Copy:
- Right-click the folder where the deleted file/folder used to reside and choose the Properties command.
- In the folder properties dialog, go to the Previous Versions tab.
- Choose the version of the folder that contains the file/folder before it was deleted, then click View.
- In the viewed folder you can access the deleted file/folder. From there you can copy it back to where it belongs.
To revert files/folders to a previous version using Shadow Copy:
- Right-click the overwritten or corrupted file and choose the Properties command.
- In the properties dialog, go to the Previous Versions tab.
- If you want to view the old version, click View. To copy the old version to another location, click Copy… To replace the current version with the older version, click Restore.
Redundant Internet (WAN Failover)

With so many key services in the cloud these days, a prolonged internet outage can be a business disaster. A simple way to reduce the likelihood of this scenario is to have redundant internet service providers—preferably with different circuit paths. Most enterprise routers even have a WAN failover feature for detecting link failure conditions and automatically re-routing traffic to the auxillary internet connection.
A few considerations for selecting redundant ISPs:
- Fiber typically offers very high speeds, is electrically isolated, and is also highly robust; drawbacks being that it is costly and vulnerable to the errant backhoe.
- 4G wireless offers decent speeds at reasonable prices in urban and suburban areas. 4G is limited by electromagnetic interference and obstructions, lower data caps, and dependence on fiber trunks beyond the broadcast area.
- Satellite offers modest speeds in remote areas. It is limited by electromagnetic interference and obstructions, lower data caps, and low upload speeds.
- DSL offers modest speeds in almost all areas that have phone service at a reasonable price. DSL is vulnerable to electrical events, weather-related line-breaks, low upload speeds, and the errant backhoe.
- Cable offers high speeds in most urban and suburban areas at a reasonable price. Cable is vulnerable to electrical events, weather-related line-breaks, and the errant backhoe.
How do I use this information?
Take fiber and DSL for instance: They’re both run in the public right-of-way, so they’re both “vulnerable to the errant backhoe.” If you teamed them up for redundancy, that would be a mistake if someone dug out a chunk of right-of-way that they both pass through. If we chose fiber and satellite, we’d probably be in better shape. If we had an electromagnetic event, the fiber would remain unaffected. If someone dug in the wrong spot, the satellite will still be fine. You get the idea.
Redundant DNS Name Servers
Traffic is routed over the internet using IP addresses, but we humans start with domain names since they are easier to remember. A DNS Name Server resolves domain names to IP addresses.
In the case of this website, your web browser used my DNS name server to resolve my domain name, eggplant.pro, to the IP address 50.77.37.41. The same mechanism is at play when you send an e-mail. What would happen if the DNS name server failed? Nothing, and that is a bad thing.
This is why if you have a website or a mail server that is mission-critical, having redundant DNS name servers (in addition to the ones provided by your domain name registrar) under your control can be a worthwhile investment.